Enabling Unencrypted TCP Connections to Lync on Port 5060
There are still many devices and clients out there that still don’t support encrypted SIP traffic over TLS like a Lync server prefers by default. In previous versions of the product allowing the server to listen on port 5060 for unencrypted TCP connections was a matter of a couple checkboxes. If you need to allow unencrypted SIP connections to a Lync server you’ll have to resort to some Management Shell work.
First, retrieve the list of registrar servers in your environment
Get-CsService -RegistrarThe output will show the identity of the registrar service along with the configured options
Identity : Registrar:fepool.ptown.local
MonitoringServer : MonitoringServer:archmon.ptown.local
ArchivingServer : ArchivingServer:archmon.ptown.local
WebServer : WebServer:fepool.ptown.local
EdgeServer : EdgeServer:edgepool.ptown.local
UserServer : UserServer:fepool.ptown.local
SipPort : 5061
WebPort : 444
SipHealthPort :
SipServerTcpPort :
EnableAutomaticFailoverFalse :
FailbackDetectionInterval :
FailureDetectionInterval :
BackupRegistrar :
DependentServiceList : {EdgeServer:edgepool.ptown.local, MediationServer:fepool.ptown.local, ApplicationServer:fepool.ptown.local}
ServiceId : 1-Registrar-1
SiteId : Site:San Francisco
PoolFqdn : fepool.ptown.local
Version : 5
Role : Registrar
You’ll notice the SipServerTcpPort parameter is null by default. We need to change this to port 5060 by running the following command:
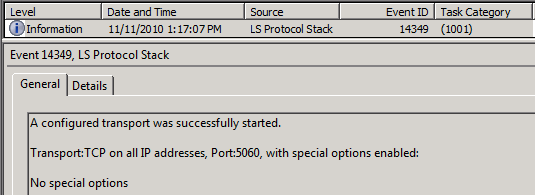
Set-CsRegistrar "registrar:fepool.ptown.local" –SipServerTcpPort 5060A big improvement over OCS here is the change does not require a restart of the services. Watch the event logs and you’ll see the Registrar service pick up this change automagically, logging Event ID 14349.
You can also run a netstat -an afterwards to verify the server is now also listening on port 5060.